Today we're having a look at how to use a ClearPass Subscriber with a Read-Only Domain Controller.
This setup is typically for branch offices where the Activate Directory and NAC services should be hosted locally to overcome WAN failures.
This post will primarily cover the "AD status:No trusted SAM account (0xc000018b)" error, when using PEAP-MSCHAPv2.
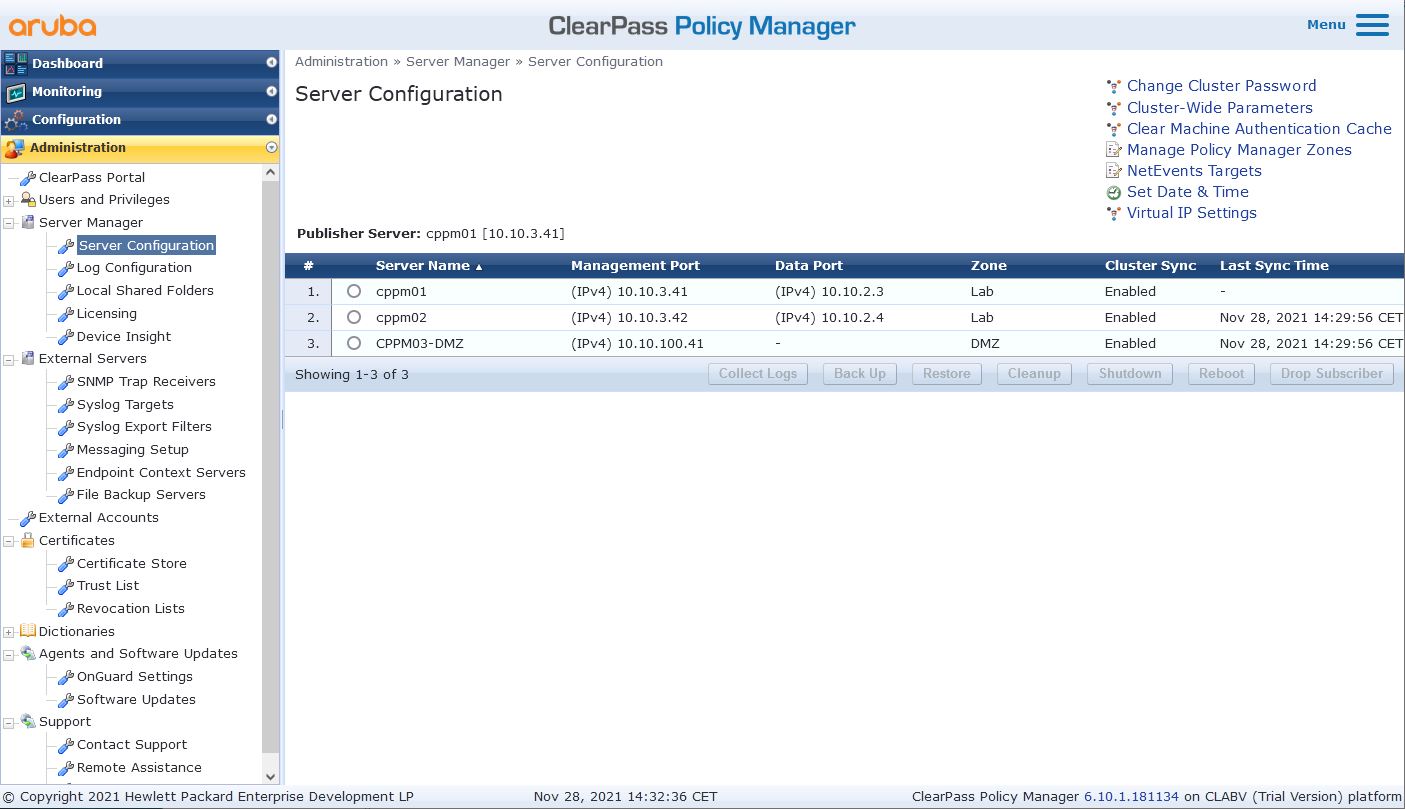
Topology:
Headquarter
2x ClearPass VMs in Zone/Active Directory Site named 'Lab'
2x Active Directory Domain Controller (writable) in Site 'Lab'
Branch
1x ClearPass VM in Zone/Active Directory Site named 'DMZ'
1x Active Directory Read-Only Domain Controller in Site 'DMZ'
 | ||
| Domainjoin with DC from another site |
If we try to join the domain with the local RODC, this operation will of cause fail, because it is just a RODC.
 | ||||
| Edit AD password servers |
After the change go to the 'Services Control' tab and restart the domain service for your domain.
AD status:No trusted SAM account (0xc000018b)
To fix this, we need to make sure that the Computer Account Object of our ClearPass Instance is synced to the RODC. To verify this and also force the AD to sync this object to the RODC, you have to look at the RODC object in 'Active Directory User and Computers'.
There you find a tab 'Password Replication Policy'. This determines which password the RODC should be able to cache.With 'Advanced...' you can view the current cached passwords.
In our case this list is fairly empty:
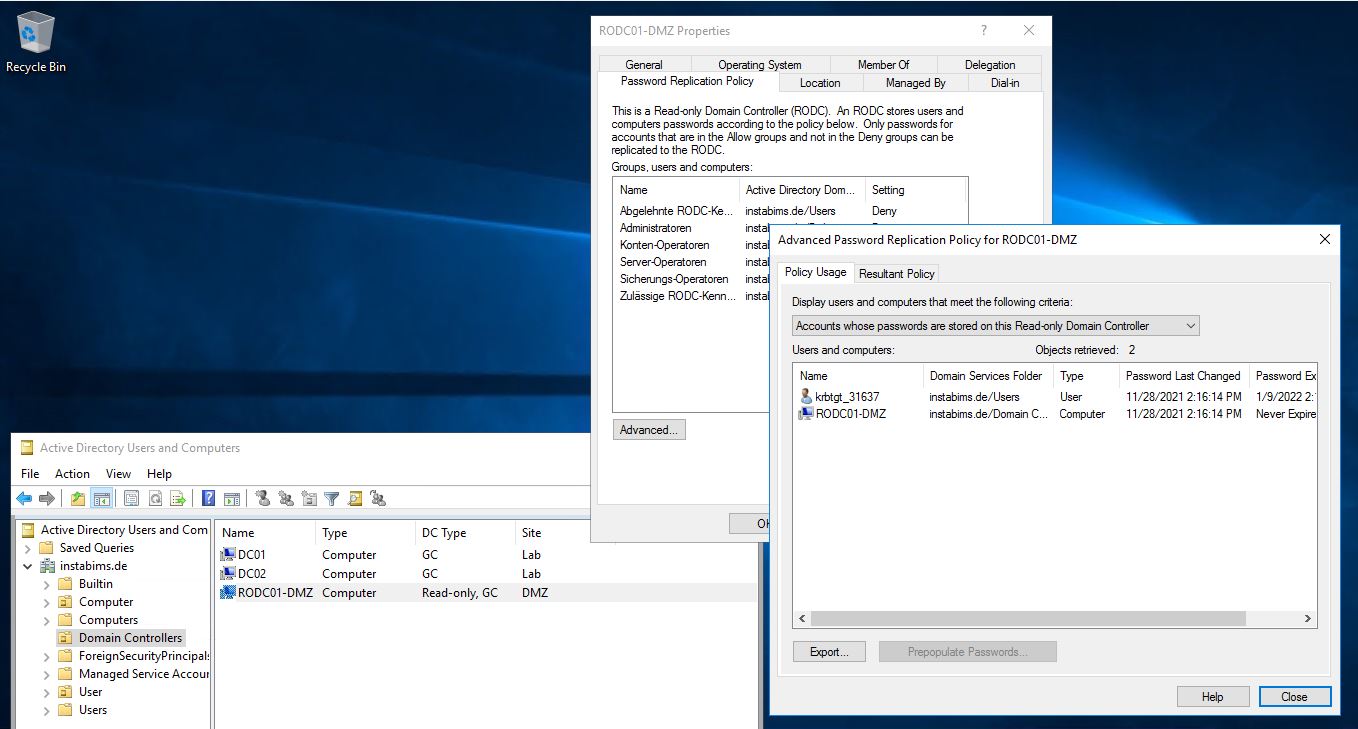 |
| RODC synced passwords before the change |
To fix the error we need to add the ClearPass AD object as 'Allowed' in the 'Password Replication Policy'. After that we can go to the 'Advanced' view and prepopulate the password to the RODC.
It should look like this:
 |
| RODC synced passwords after the change |
Now the error during authentication should be gone!
You can verify MSCHAPv2 via the ClearPass CLI as 'appadmin' user with the commands:
ad auth -u <USER> -n NETBIOS-DOMAINNAME
krb auth <USER>@domain
Please be aware, that if you use the AD as 'Authentication Source' via LDAP you also need to think about which primary DCs and which backup DCs to use.
With many branches you probably want to create one Authentication Source per branch and use different ClearPass services per branch.
Also you should try to get rid of EAP-PEAP and work towards EAP-TLS :-)